- Mozilla_pkix_error_mitm_detected Allow
- Mozilla_pkix_error_mitm_detected Windows 10
- Mozilla_pkix_error_mitm_detected Corporate Proxy
- Mozilla_pkix_error_mitm_detected Windows 10
- Mozilla_pkix_error_mitm_detected Ubuntu
Press J to jump to the feed. Press question mark to learn the rest of the keyboard shortcuts. It’s essential to make sure that the websites you browse are secure. There are a few ways that you can check this. One is by looking for the lock symbol.
- 1Installing Certificates Into Firefox
- 1.2Built-in Windows and MacOS Support
There are lots of organizations that use their own private certificate authorities (CAs) to issue certificates for their internal servers. Browsers that attempt to validate certificates issued by a private CA certificate will display errors unless they are configured to recognize these certificates. Since Firefox does not use the operating system's certificate store by default, these CA certificates must be added in to Firefox using one of the following methods.
Import via Policy
As of Firefox 64, an enterprise policy can be used to add CA certificates to Firefox. This is now the method recommended for organizations to install private trust anchors.
The ImportEnterpriseRoots key will cause Firefox to trust root certificates that are in the system certificate store as long as the key is set to “true”. We recommend this option to add trust for a private PKI to Firefox. It is equivalent to setting the 'security.enterprise_roots.enabled' preference as described in the next section.
The Install key by default will search for certificates in the locations listed below. Starting in Firefox 65, you can specify a fully qualified path (see cert3.der and cert4.pem in this example). If Firefox does not find something at your fully qualified path, it will search the default directories.
Certificates can be located in the following locations:
- Windows
- %USERPROFILE%AppDataLocalMozillaCertificates
- %USERPROFILE%AppDataRoamingMozillaCertificates
- MacOS
- /Library/Application Support/Mozilla/Certificates
- ~/Library/Application Support/Mozilla/Certificates
- Linux
- /usr/lib/mozilla/certificates
- /usr/lib64/mozilla/certificates
- ~/.mozilla/certificates
Built-in Windows and MacOS Support
Windows and MacOS enterprise root support can be enabled by setting the 'security.enterprise_roots.enabled Get on topgaming potatoes. ' preference to true in about:config.
Windows Enterprise Support
As of version 49, Firefox can be configured to automatically search for and import CAs that have been added to the Windows certificate store by a user or administrator. To do so, set the preference 'security.enterprise_roots.enabled' to true. In this mode, Firefox will inspect the HKLMSOFTWAREMicrosoftSystemCertificates registry location (corresponding to the API flag CERT_SYSTEM_STORE_LOCAL_MACHINE) for CAs that are trusted to issue certificates for TLS web server authentication. Any such CAs will be imported and trusted by Firefox, although note that they may not appear in the Firefox's certificate manager. It is expected that administration of these CAs (e.g. trust configuration) will occur via built-in Windows tools or other 3rd party utilities. Note also that for such configuration changes to take effect in Firefox either the preference will have to be toggled off and on again or Firefox will have to be restarted.As of version 52, Firefox will also search the registry locations HKLMSOFTWAREPoliciesMicrosoftSystemCertificatesRootCertificates and HKLMSOFTWAREMicrosoftEnterpriseCertificatesRootCertificates (corresponding to the API flags CERT_SYSTEM_STORE_LOCAL_MACHINE_GROUP_POLICY and CERT_SYSTEM_STORE_LOCAL_MACHINE_ENTERPRISE, respectively).

Note: As of this writing, this setting only imports certificates from the Windows Trusted Root Certification Authorities store, not corresponding Intermediate Certification Authorities store. See bug 1473573. If you are experiencing “unknown issuer” errors even after enabling this feature, try configuring your TLS server to include the necessary intermediate certificates in the TLS handshake.
MacOS Enterprise Support
As of Firefox 63, this feature also works for MacOS by importing roots found in the MacOS system keychain.
Linux
On Linux, certificates can be programmatically imported by using p11-kit-trust.so from p11-kit (add the module using the “Security Devices” manager in Preferences or using the modutil utility).
Preload the Certificate Databases
Some people create a new profile in Firefox, manually install the certificates they need, and then distribute the various db files (cert9.db, key4.db and secmod.db) into new profiles using this method. This is not the recommended approach, and this method only works for new profiles.

Certutil
If you're a real diehard, you can use certutil to update the Firefox certificate databases from the command line.
Credits
The original content of this wiki page was copied (with permission) from Mike Kaply's Blog.

Mozilla_pkix_error_mitm_detected Allow
A Certification Authority (CA) is an organization that browser vendors (like Mozilla) trust to issue certificates to websites. Last year, Mozilla published and discussed a set of issues with one of the oldest and largest CAs run by Symantec. The discussion resulted in the adoption of a consensus proposal to gradually remove trust in all Symantec TLS/SSL certificates from Firefox. The proposal includes a number of phases designed to minimize the impact of the change to Firefox users:
Mozilla_pkix_error_mitm_detected Windows 10
- January 2018 (Firefox 58): Notices in the Browser Console warn about Symantec certificates issued before 2016-06-01, to encourage site owners to replace their TLS certificates.
- May 2018 (Firefox 60): Websites will show an untrusted connection error if they use a TLS certificate issued before 2016-06-01 that chains up to a Symantec root certificate.
- October 2018 (Firefox 63): Distrust of Symantec root certificates for website server TLS authentication.
After the consensus proposal was adopted, the Symantec CA was acquired by DigiCert; however, that fact has not changed Mozilla’s commitment to implement the proposal.
Firefox 60 is expected to enter Beta on March 13th carrying with it the removal of trust for Symantec certificates issued prior to June 1st, 2016, with the exception of certificates issued by a few subordinate CAs that are controlled by Apple and Google. This change affects all Symantec brands including GeoTrust, RapidSSL, Thawte, and VeriSign. The change is already in effect in Firefox Nightly.
Mozilla_pkix_error_mitm_detected Corporate Proxy
Mozilla telemetry currently shows that a significant number of sites – roughly 1% of the top one million – are still using TLS certificates that are no longer trusted in Firefox 60. While the number of affected sites has been declining steadily, we do not expect every website to be updated prior to the Beta release of Firefox 60. We strongly encourage operators of affected sites to take immediate action to replace these certificates.
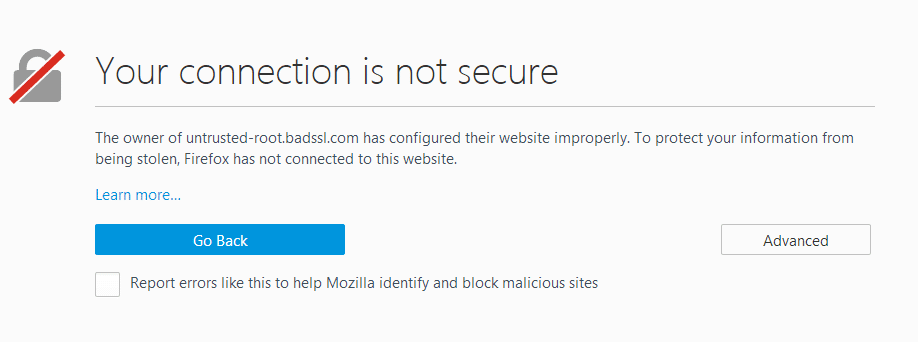
If you attempt to visit a site that is using a TLS certificate that is no longer trusted in Firefox 60, you will encounter the following error:
Mozilla_pkix_error_mitm_detected Windows 10

Clicking on the “Advanced” button will allow you to bypass the error and reach the site:
These changes are expected to be included in the final version of Firefox 60 that is planned to be release on May 9th, 2018.
In Firefox 63, trust will be removed for all Symantec TLS certificates regardless of the date issued (with the exception of certificates issued by Apple and Google subordinate CAs as described above).
Steptronic is the name BMW gives its automatic transmissions that have a manual shift function, which is pretty much any automatic-equipped BMW. Even though it’s an automatic, you can upshift and downshift on command when the gear selector is in a separate shifter gate, which can be accessed by pulling the gear selector to the left. Porsche has the PDK transmission; Audi has the DSG transmission; and BMW has the Steptronic. To make the BMW sporty and appeal to those drivers that love a manual transmission, BMW has developed an automatic transmission called the 'Steptronic.' This transmission has three modes, including a comfortable Drive. This video is about how to use the BMW steptronic transmission and how to start and select Drive,Reverse,Neutral,Park,Sports, and manual and how to select ec. Extremely fast gear changes, a high degree of shift comfort and optimised efficiency – these are the benefits of the 7-speed Steptronic automatic transmission with double clutch, available for the MINI 3 door, the MINI 5 door and the MINI Convertible. Steptronic transmission bmw explained. Steptronic is a function of manual gear shifting on an automatic transmission.It was created by the ZF Friedrichshafen AG German manufacturer, based on BMW’s design in 1996. It can be seen on BMW, Mini, MG and Rover cars. The gearbox can be controlled using the.
Mozilla_pkix_error_mitm_detected Ubuntu
Wayne Thayer
Kathleen Wilson